From A to Z, separating the internet network from the internal network and information exchange between them.
What is the segregation of the Internet network from the internal network and why should this be done?
Residential houses in the old days had two inner and outer sections in order to maintain more privacy, and only confidant was allowed to enter the inner part of the house. In the same way, to increase the security of information in organizations and companies today, and to prevent all kinds of security threats that may happen through the Internet in the form of hack, ransomware, viruses, Trojans, or any kind of intrusion and security threats, security specialists strongly recommends that the entire internal network of an organization should be isolated. And users who need the Internet should use it on a completely independent network, so that the organization is safe from such security threats.
In the following, we will explain all the eight methods of separating the Internet network from the internal network, examine their advantages and disadvantages, and explain the prerequisites necessary to benefit from each one, and then we will discuss how to establish communication between these two networks.
types of separation of internet network from internal network methods
Description:
In this method, each user is given 2 computers along with a KVM switch device. so that he can switch between his Internet computer and his corporate computer.
Or that each user is provided with 2 complete computers (2 mouse, keyboard, monitor and computer), each of these computers is connected to an isolated network.
Executive requirements:
– Two completely independent and separate network platforms.
– Dual IT support force.
– Large desks for users, so that it has the capacity of two computers.
Cost:
The cost of providing a computer with a KVM switch will be more than 200 dollars.
Advantages:
This method has no advantages compared to other methods.
Disadvantages:
All the problems you have had in the IT department of your organization so far will be multiplied by 2.5 by choosing this method!
Because in addition to the doubling of the computers, new computers need more support to secure information because they are connected to the Internet.
And besides, the problems of using KVM also add to the story, hence the estimated number of 2.5 was mentioned.
Who are the audience of this method?؟
A- Companies that have redundant computer due to the lay offs.
B- Companies that are not familiar with other methods!
For the reasons mentioned above, Raha not only does not recommend this method, but also does not provide any services to implement it.
Description:
In this method, the computer hard drive is separated from the motherboard, and with another hard drive or SSD is connected to an isolator card.
And the isolator card is installed on the motherboard and a separate operating system is installed on each of these two hard drives (or SSD).
In addition, each isolator card also has 2 network cards, which every time the power of this card is disconnected and connected (computer restart), the computer is booted with one of the hard drives and network cards.
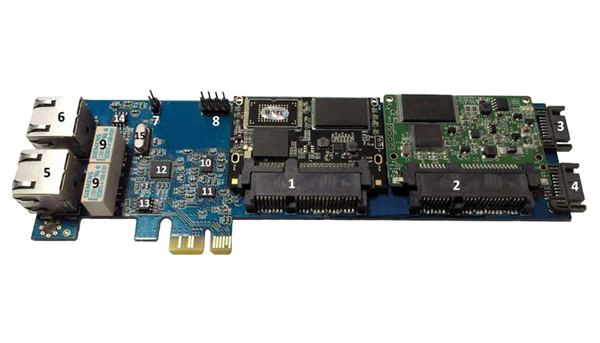
Below you can see an example of an isolator card with its components:
1 and 2: Connection point of two SSDs to install two operating systems
3 and 4: the connection point of two hard disks or CD-ROMs
5 and 6 the connection point of two network cables
7 and 8: Mode change jumper
9: network disconnection relays
10: Switcher in SSD slots
11: Switcher of SATA 3 and 4 ports
12: Chipset command switch to switchers No. 10, 11, and 13 (changes the switchers every time the power is turned off and on.)
13: Command switcher to network relays
Executive requirements:
Two completely independent separate network platforms.
Cost:
The cost of providing one card along with two SSDs with a capacity of at least 64 gigs to install the operating system is about $180.
Advantages:
This method is the cheapest among physical separation methods (other than VDI).
Disadvantages:
To switch between two networks, the system must be restarted once, and it takes about 15 seconds.
If the performance of any of the parts number 9 to 13 is disturbed, there is a possibility of connection between the two networks, and this is considered a security hole.
The average lifespan of these cards is two years (due to many disconnections and restarts).
Many users are dissatisfied because of these frequent restarts.
Who are the audience of this method?؟
A- Since this method is old, most of the contacts of this method are those who turned to this method at the very beginning of the separation security directive.
B- companies that are not familiar with other methods!
Since the beginning of 2018, Raha no longer produces this product due to the customers lack of interest in this product.
Description:
In this method, assuming that the users have a computer device, we provide them with a zero client along with a KVM switch to use the Internet. that the zero client is connected to the Internet server through the second network platform and the user can switch between their computer and the zero client in real time through KVM.
Executive requirements:
Two completely independent separate network platforms. (You can use the limited wireless network for the Internet)
– Server for zero clients. For 100 users with a concurrency factor of 60% (it means that at the moment 60% of users apply workload on the server. In government organizations, the concurrency factor is 60% and it is 80% in private organizations).
30 processor threads and 100 GB of RAM and storage with 150K IOps and 256 GB of capacity are required. The bandwidth required by each user is between 30 and 2000 KB (depending on the type of communication protocol). For more specialized information, refer to the attached virtualization proposal.
Cost:
The cost of a zero client along with a KVM device and the server cost for each user is approximately $190.
Advantages:
Note that these advantages are compared to the previous methods.
Higher information security.
The user can instantly switch between two networks.
Fast implementation and without disruption with the existing infrastructure of the employer, along with many management and monitoring options.
Disadvantages:
Except in the cases that it has led to the managers and users’ dissatisfaction, due to inappropriate choice of platform and improper protocol implementation. This method does not have any problems by itself, but newer methods are more optimal.
Who are the audience of this method?
This method is completely standard and principled, but with the growth of virtual methods, it has given its place to virtual methods, and now it is in the second position among the methods. Due to the variety of zero clients (PC-Sharing, VDI) and types of communication protocols, this method has a lot of implementation variety, and refer to the attached virtualization proposal to check their types.
Many parameters must be checked in choosing the right method for each organization. Including the network infrastructure, the number of users, the needs of the employer’s IT unit, the security and management requirements, and the cost, so it is recommended to study all the different separation methods first, if you choose this method, you must study the attached virtualization proposal in detail. And keep in mind that Raha experts are always by your side to provide expert advice in choosing the most suitable solution.
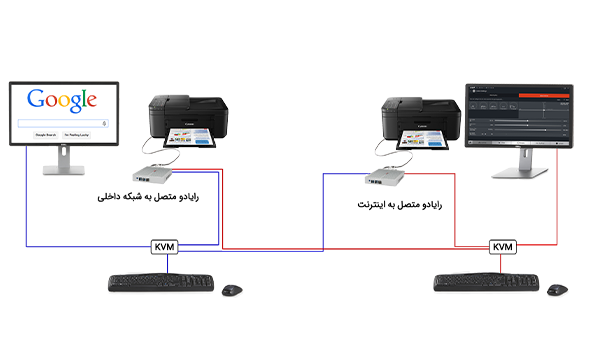
Description:
This method is one of the most widely used methods. And each user is assigned two zero clients along with a KVM Switch device to operate in two isolated environments (intranet and internet).
Executive requirements:
Two completely independent separate network platforms. (For the internet network, you can use the limited wireless network)
Server for zero clients. for 100 users (2 zero clients for each user) with a 60% concurrency factor (that is, 60% of the users apply workload
on the server at the moment the concurrency factor in government organizations is 60% and it is 80% in private organizations.) 50 processor threads and 160 GB of RAM and storage with 200K IOps and 500 GB of capacity are required and the bandwidth required by each user is between 30 and 2000 KB. (Depending on the type of communication protocol) For more specialized information, refer to the attached virtualization proposal.
Cost:
The cost of two zero clients along with a KVM device and the server cost for each user is approximately $320.
Advantages:
– The highest information security factor.
– The user can instantly switch between two networks.
– Fast implementation, and the highest monitoring and management options.
Disadvantages:
Except in the cases where due to inappropriate choice of platform and protocol and improper implementation, it has leads to the managers and users’ dissatisfaction.
This method does not have any problems by itself, but newer methods are more optimal.
Who are the audience of this method?
This method is completely standard and principled, but with the growth of virtual methods, it has given its place to virtual methods, and now it is in the second position among the methods. Due to the variety of zero clients (PC-Sharing, VDI) and types of communication protocols, this method has a lot of implementation variety, and refer to the attached virtualization proposal to check their types. Many parameters must be checked in choosing the right method for each organization. Including the network infrastructure, the number of users, the needs of the employer’s IT unit, the security and management requirements, and the cost, so it is recommended to study all the different separation methods first, if you choose this method, you must study the attached virtualization proposal in detail.
And keep in mind that Raha experts are always by your side to provide expert advice in choosing the most suitable solution.
Description:
Raya2 is actually the second generation of computers that can be used by two people at the same time. And its purpose is to separate the internal network from the Internet in such a way that two devices will be assign to both users. According to the picture below, each of them is connected to one of the networks and both users are connected to both of them simultaneously by a KVM Switch as shown below.
Executive requirements:
Considering that there are 2 network links in each set for both users, no infrastructure requirements are needed in this method.
It is enough to connect one of the network cables to the internal network and the other to the Internet network on the side of the distribution racks.
Cost:
According to the above image scenario, two Raya2 devices are needed for two users near each other, the cost of each Raya2 device is about 200 dollars.
Advantages:
There is no need to create an independent physical network.
Disadvantages:
In this method, we will still face the problems of preserving computers and thin clients, and in zero client-based methods, we will not need to service users and their devices.
Who are the audience of this method?
This method is suitable for companies that are not able to implement VDI platform or provide zero client for any reason.
Description:
This method is the most popular and the best method of separating the Internet from the internal network. In this way, the users in the organization see some Internet browser icons on their desktop, which is provided to them through VDI from an isolated server, and no there is no information exchange between these browsers and their desktop. And in fact, they are viewing the image of those web pages that are only on a specific and limited port in the form of packets that have no informational value. (For more information in this regard, see the virtualization proposal on page 88 of the attachment).
Executive requirements:
It is recommended to separate the VDI-Virtual App network from the internal network as much as possible. For example, by distributing it on a wireless platform and assigning a WIFI USB Adapter to each user or even another network card. The mentioned separate network can be completely limited through different types of protocols so that there is no information flow on that network. And only the coordinates of the pixels that are changing are encrypted and sent to each user.
Such packages do not have any informational value even if the encryption or compression method is leaked, and the intruder cannot even watch the image that each user is viewing.
Hardware resources on the server for every 100 Internet users, with a 60% concurrency factor, equal to 64 GB of RAM, 30 processor threads, and 150 KIOps for storage.
Cost:
The cost of providing hardware resources on the server is approximately 40 dollars for each user.
Advantages:
– Fast implementation, and the highest monitoring and management options.
– Each user has a completely isolated access to the Internet on the same desktop.
– There is no need to provide any hardware to the users, and all software services to them are also done through the network.
Disadvantages:
Sometimes there are strictures that do not accept information security in this solution. But keep in mind that South Korean and American governments use this method. And besides that, no penetration report of this solution has been published worldwide. And from a logical point of view, there is no possibility of penetration in case of correct and principled implementation.
Who are the audience of this method?
All companies where the new spirit of information technology without biases is flowing in them are the interested audiences of this solution.
For security reasons, it is highly recommended to entrust the implementation of this solution to companies that are experts in security in addition to virtualization knowledge.
and have a security certificate of information security management audit, and have a decent resume in such projects.
Description:
This method is exactly the same as the method of assigning two zero clients to each user, with the difference that two zero clients along with a KVM Switch device in one box and in the form of a product called SCATIN were produced and presented to the market by Raha Group.
Due to the different needs of organizations in choosing the type of zero client, as well as the high cost of this product due to the low circulation, Raha no longer produces this product, so it is recommended to use other solutions. This device was initially (in 2017) commissioned by the Ministry of Interior and produced by Raha Company.
Description:
The word DTC stands for Dual Thin Client and it means that in this device, two Thin Clients and a KVM Switch are placed in one case.
And in fact, it is the same as method number 1, with the difference that instead of two large computers, two small computers are used in the form of a case, and all the advantages and disadvantages of this solution are the same as solution number 1.
Since the beginning of 2019, Raha no longer produces this product due to the customers lack of interest in this product.
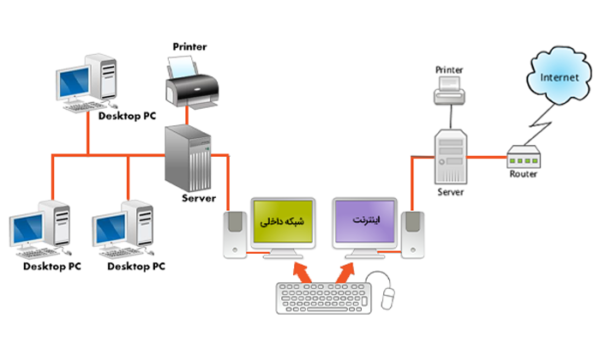
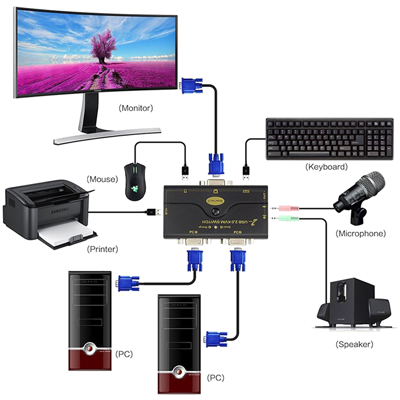
۱ـ KVM Switch:
It is a small device (the size of a mobile phone) and cheap (5-10$) through which you can control several computers with a mouse and keyboard and view their image on a monitor. This device works in such a way that it switches between two computers by pressing a key on the keyboard or a key on the KVM itself.
2- Computer:
A computer can be Fat Client or regular computers or Thin Client, so be careful that the computer means all the devices on which the operating system (for example Windows) is installed directly on them, such as a case, thin client, laptop, minicomputer.
3- Zero client:
Unfortunately, many people confuse zero clients with thin clients, while thin clients fall under the category of independent computers (explained above), but zero clients are devices that are designed to serve their users and they must be connected to a server, and in fact they cannot provide any service to their users alone and independently, and have nothing of their own (zero = 0).
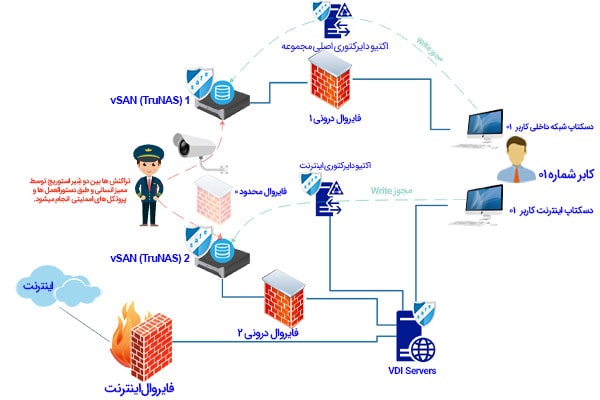
maintaining communication between two isolated network (best method suitable for all methods)
Now it is assumed that you have succeeded in separating the Internet network from the internal network through one of the 8 methods.
But many companies face this requirement, that users need to transfer files and information from the Internet to internal network computers or vice versa, that is, they can transfer files or information from the internal network to the Internet, and this is exactly It is a tragedy for information security experts
There are only two methods to solve this issue, the human and automatic audit method, which basically do not have much difference in the infrastructure, an attempt has been made to explain this issue in the following two forms.
(For more information about the scenarios, contact your support expert to have a conference with the company’s security expert)
The first method – without human audit
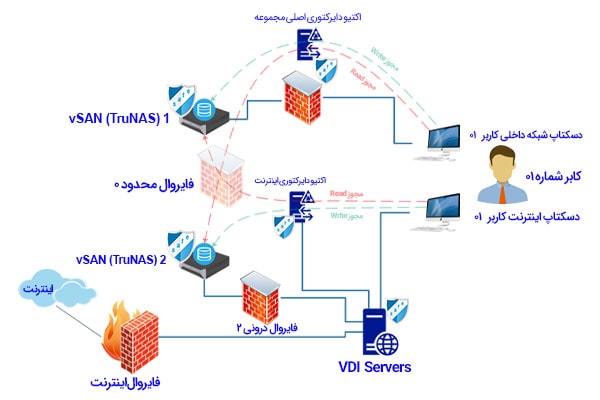
The second method – with human audit