Unified network and threats management system Raha UTM
What is UTM?
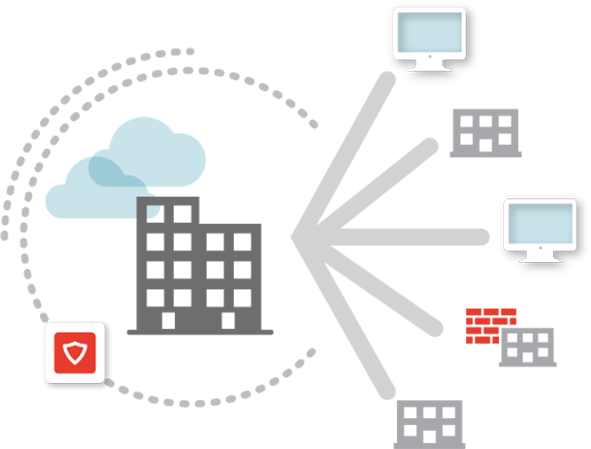
Unified Threat Management is a unified threat management system.
This system is in the category of 3rd generation firewalls, which are also called Next-Generation Firewall (NGFW).
And the meaning of their integration is that in these systems, various monitoring, management and security systems are also embedded, in addition to the firewall.
And Raha!
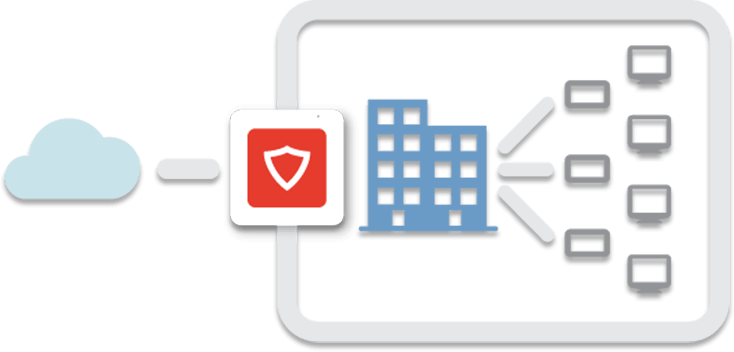
Linux base system, unified threat management system based on Kerio, SOPHOS and Bitdefender
security products is a comprehensive security, monitoring and management solution that makes you needless from other types of products.
In general, this system meets the needs of all small and large companies, which in addition to the role of all products and hardware it plays such as:
- Mikrotik
- Peplink
- Firewall
- WAF
- Router
- Cache Server
- Proxy Server
- VPN Server
- Full Option DHCP Server
- …
It does much more completely and optimally than them, so that you will not need any of the above products for your monitoring, management and security needs even in the future.
And if you already have some of the above hardware in your network, you can safely remove them by installing this system.
For example, load balance between your internet lines much better than a hardware device called Peplink which is specially designed for this task.
Attractive features of the UTM system
In addition, the unified threat management system also provides managers with other useful features in the form of a system with a user-friendly work environment.
So that you can apply any policy with minimal network knowledge very quickly.
In the following, we will discuss some of the attractive features of the UTM system and explain each one in detail:
Last word:
Finally, it should be noted that the items mentioned above may sometimes be introduced as options in some products similar to UTM.
But be careful that simply mentioning them as an option is not a proof of their performance quality and ease of use.
Integrating all these things in the threat management system together is a very complex and sensitive issue.
The coordination and stability of their performance together with each other is the result of too much time and a very large community of customers and consumers.
That the manufacturer can find more problems and bugs in their system every day by getting feedback and solve them with the help of a large and expert team.
Therefore, Iranian products in this field are not comparable to global products of reputable companies such as Kerio, SOPHOS, FortiGate, Bitdefender in terms of the number of consumers.
Therefore, it is obvious that it cannot be compared with them in terms of quality and efficiency, so the best advice of Raha company is to get your unified threat management system only from the mentioned companies and don’t be satisfied with providing it!
This means that preparing this system is only 20% of the story and the remaining 80% is its specialized and precise configuration.
So don’t feel relieved for just having this product, even if you have bought it from the manufacturing company itself,
Leave its configuration and setup to an experienced team.
Raha, with more than 20 years of experience in the field of IT and information security, is at your side with the help of an expert’s team with international degrees, including information security management audit.
In order to comply with the security requirements regarding your system configuration and finally provide a report of the status and configuration map and the result of the penetration test of your network.