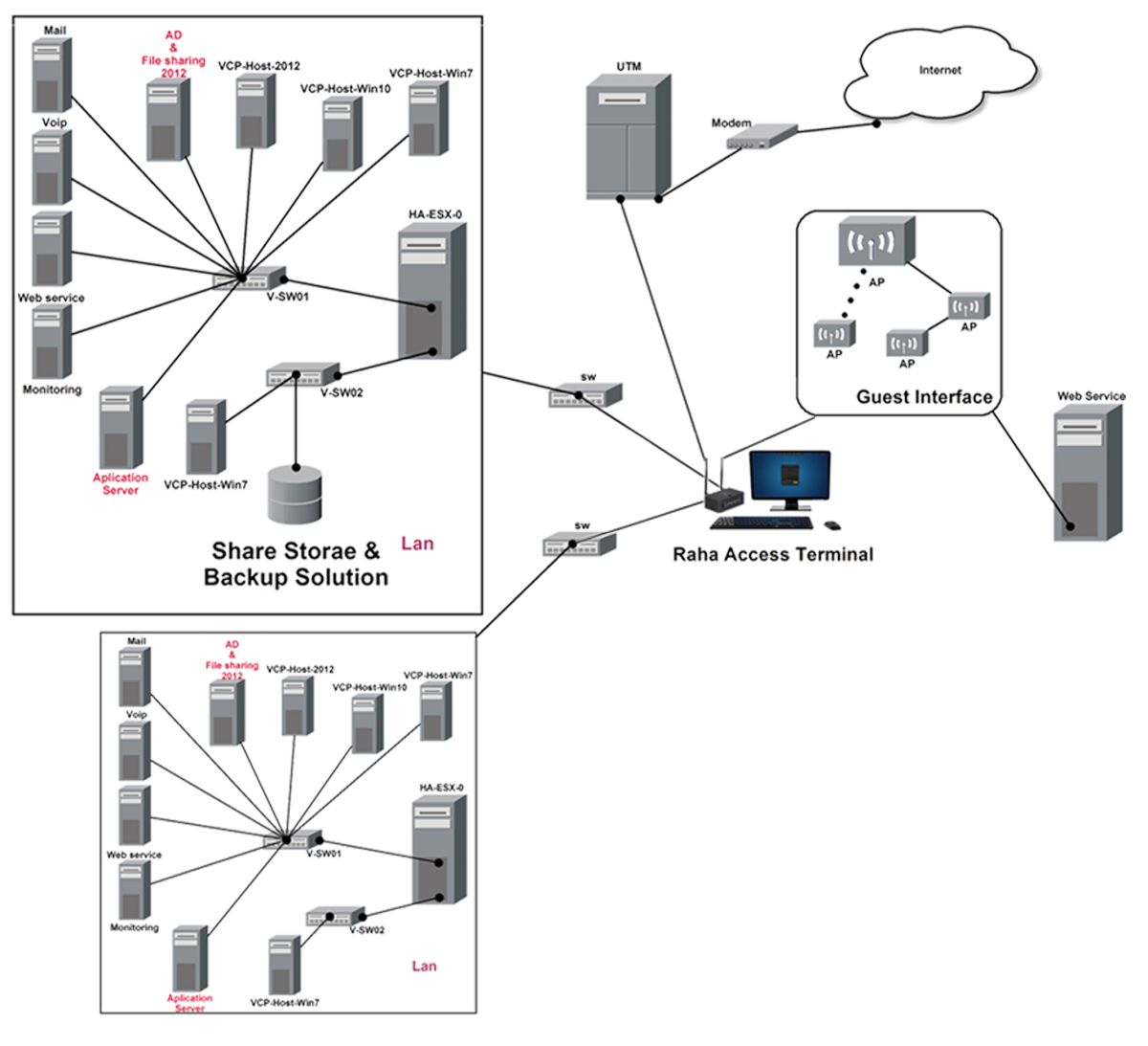
What is S-CATIN?
Secure Concurrent Access Terminal for Isolated Networks, this devices family (i20 and i22, j22) are based on the RahaCo’s production. (Patented, with Iran Code, with various technical and security approvals) that are suitable for companies that have the following concerns:
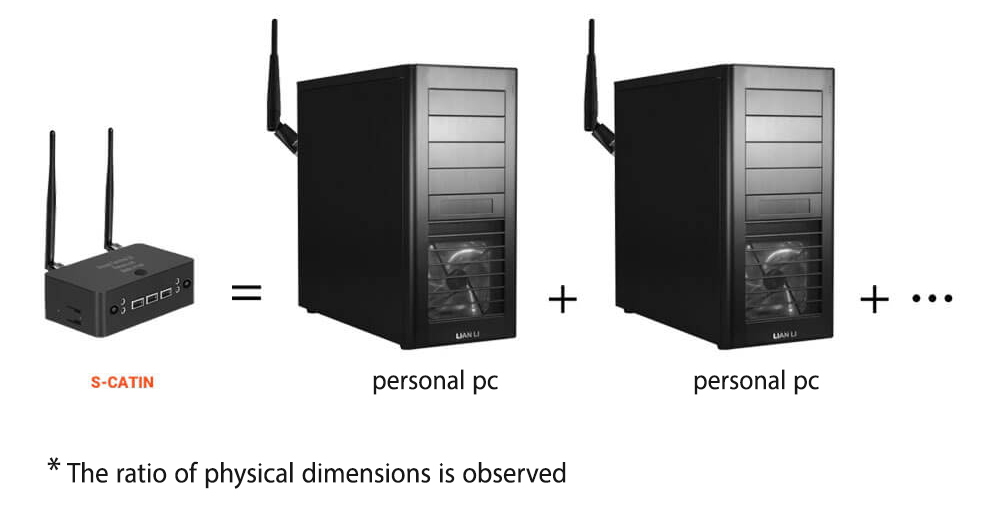
This device with the physical dimensions seen in the figure (compared to a normal computer) whose name is S-CATIN (SECURE CONCURRENT ACCESS TERMINAL FOR ISOLATED NETWORKS) works like two independent computer devices. which can be connected to 4 completely independent networks at the same time (through 2 cable links and 2 wireless links) and allows us to work with four completely independent working environments at the same time and switch between them in less than 2 seconds do.
S-CATIN network isolator capabilities



I series devices work based on DDP protocol and J series devices are based on other virtualization protocols.
Comparison table of types of insulators
And now we address the point that; What is the difference between S-CATIN models? And we look at the difference between S-CATIN network isolators.
| features | isolator j22 | isolator i20 | isolator i22 |
|---|---|---|---|
| manufactor country | UK | China | China |
| warranty (year) | 3 | 3 | 3 |
| validity of purchase | 8/10 | 9/10 | 9/10 |
| particular features | change in hardware and software according to the customer needs | – | – |
| disadvantages | not having brocket | – | – |
| Hardware quality | 8/10 | 8/10 | 8/10 |
| dimension | |||
| DDP | – | DDP | DDP |
| PCoIP | PCoIP | – | – |
| Citrix | Citrix | – | – |
| RDP | RDP | – | – |
| particular protocols | 2X-Docker | – | – |
| Stability in use | An average of 0.7 outages in an 8-hour period in office use | Average 0.3 outages in an 8-hour period in office use | Average 0.3 outages in an 8-hour period in office use |
| CPU | 4*1.2GHz | 4*1.2GHz | 4*1.2GHz |
| Ram | 2*1GB | 2*1GB | 2*1GB |
| internal memory | – | – | – |
| Ability to change hardware | yes | no | no |
| Average network bandwidth usage | |||
| input Output | USB2*8-2*VGA/HDMI-2*LAN-Bluetooth-WiFi | USB2*8-2*VGA-2*LAN | USB2*8-2*VGA-2*LAN- -2*wifi |
| The number of possible users on one core/thread of the host CPU for office users | 2.5 | 3.5 | 3.5 |
| The number of possible users on one core/thread of CPU for professional users | 2 | 2.5 | 2.5 |
| The amount of RAM required for an office user | 1 | 1 | 1 |
| The amount of RAM required for a professional user | 2 | 1.5 | 1.5 |
| Full HD video playback | * | * | * |
| HD video playback | * | * | * |
| Compatibility with USB peripherals | 8/10 | 9/10 | 9/10 |
| Suitable for use under 10 people | Due to special infrastructure, it is not economical | Appropriate | Appropriate |
| Suitable for use under 20 people | Due to special infrastructure, it is not economical | Appropriate | Appropriate |
| Suitable for use under 20-30 people | Appropriate | Appropriate | Appropriate |
| Suitable for use under 30-50 people | Appropriate | Appropriate | Appropriate |
| Suitable for use more than 50 people | Appropriate | Appropriate | Appropriate |
| price | 13,000,000 | 15,000,000 | 17,000,000 |